What Is Account Takeover Fraud?
Financial services organizations need and want to protect their customers’ accounts from unauthorized use, including account takeover fraud

Account takeover fraud (ATO) occurs when an unauthorized person takes control of an account. The fraudster takes steps to actively control the account, for example by applying for a new card or changing the account contact information or password. In this post I’ll talk specifically about account takeover in financial services and the steps that can be taken to detect, prevent and mitigate against it.
While individuals are frequently the victims of account takeover fraud, businesses, particularly small businesses, can be as well. The CIFAS Fraudscape for 2025 reported that 18% of cases reported to the national fraud database were account takeover cases.
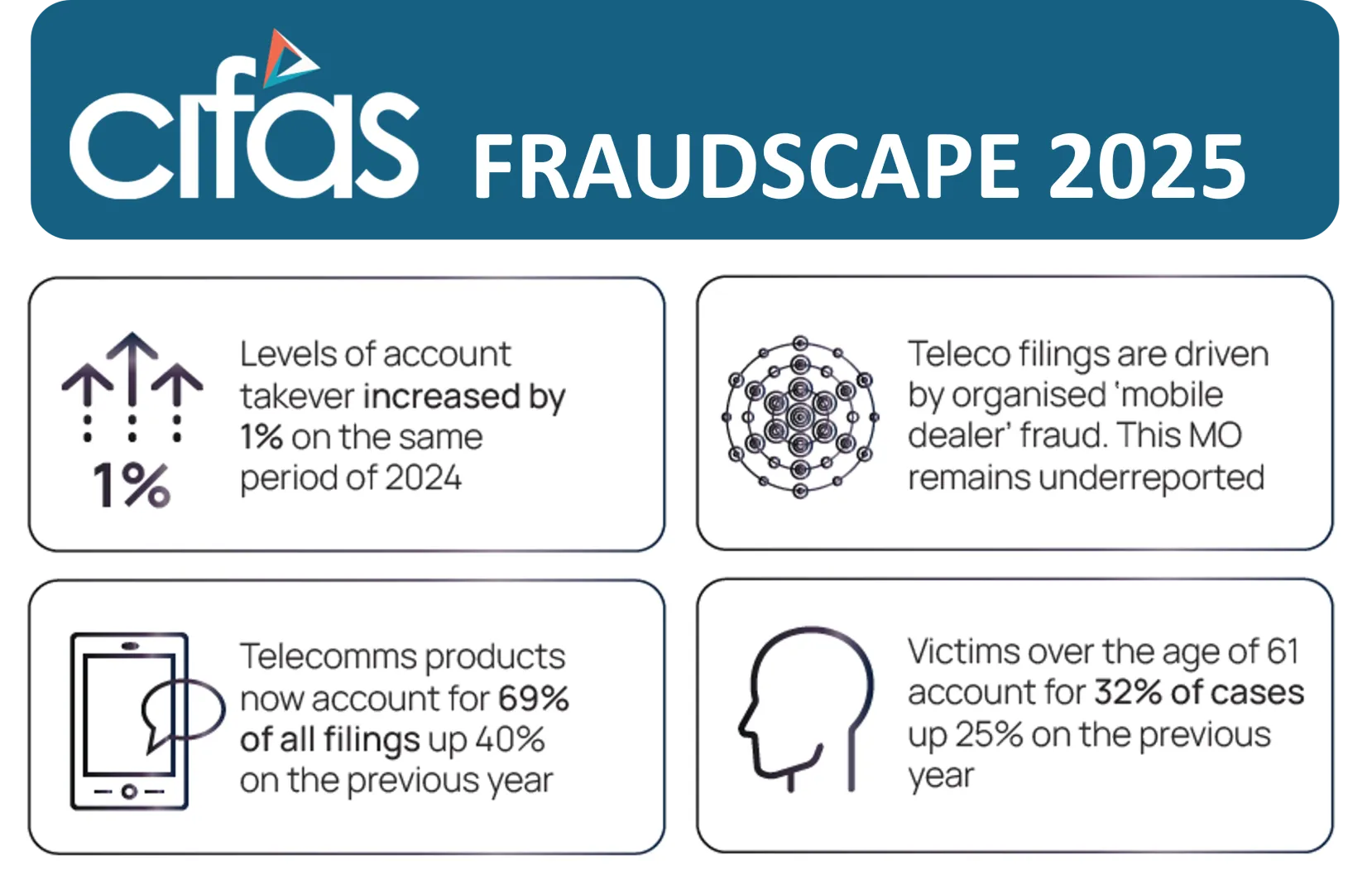
Source: Fraudscape 2025 - Cifas
ATO – Old School and High-Tech
Account takeover fraud is nothing new, but in the past criminals were reliant on more manual ways to collect enough knowledge about a victim in order to access and then take control of their accounts. Trawling through people’s trash, stealing mail, and bribing or applying pressure to the employees of financial institutions to disclose customer data were their predominant routes to success.
While these methods are still used now, developments in recent years have made things much easier for the criminals. Today’s world of cybercrime means that fraudsters can buy enough information about people and their finances from the dark web to enable them to take over financial accounts.
The dark web offers a marketplace for the data stolen in data breaches and 2021 made it a record-breaking year with significant data breaches around the world, leading to the loss of many millions of personal records.
The data available for purchase on the dark web can be very rich; personal information such as date of birth, email address, Social Security number / national ID and phone number are sold alongside account specific information such as usernames and passwords. As people frequently use the same passwords across multiple accounts, the theft of one account’s information can make all their accounts vulnerable.
With large volumes of data at their disposal, the fraudsters then need to test it, to find out if they can actually access accounts. Once more, there are old-school and high-tech routes to do this. They can use automated tools to mount mass attempts to access accounts with credential stuffing. But this is not the only way they are succeeding; the CIFAS report notes that 44% of account takeovers took place using telephony channels, suggesting that call centers might be perceived as a weak link.
What Do Fraudsters Do with Accounts They Have Taken Over?
Fraud exists within a supply chain. The criminals that committed a data breach to access records are not the same criminals that use the data to determine if an account is accessible. Similarly, having tested the data and found the vulnerable accounts, those criminals frequently sell on the account records to other fraudsters that then take over the account.
What happens next varies. Some fraudsters are looking for a quick return on their investment and simply transfer available funds to accounts in their control – often through the use of networks of money mules.
Other fraudsters are playing a longer game, looking to leverage the account they have taken over to maximize gains. This is a process that can include several steps:
- They establish longer-term control of the account, for example by changing account details such as address, mobile phone number and date of birth.
- They have a card for the account re-issued with their details and sent to an address (such as a mailbox) they control.
- They use the account they have taken over to maximize the funds available to them, for example by increasing credit limits or by using the account as a gateway to open more lucrative accounts such as a loan. Once they judge they have maximized the amount they can obtain before the risk to them becomes too high, they cash out by transferring all the funds to accounts under their control.
When this happens it is extremely difficult for the financial institution to separate the legitimate account holder from the fraudster and determine what account activity was carried out by whom. Financial institutions also have to deal with significant issues of first-party fraud, so can’t make too many assumptions about apparent cases of account takeover. It can be a long and distressing process for a legitimate accountholder who can’t prove their account ownership.
How Can Financial Institutions Tackle Account Takeover Fraud?
Stopping account takeover fraud means both preventing it from happening and detecting suspicious activity so that intervention can happen.
Strong customer authentication
Identity authentication is a big part of account protection and banks, and other financial institutions place a great deal of emphasis on protecting the log-in process. In the European Union, PSD2 regulation for strong customer authentication is perhaps more frequently associated with checking a customer’s identity when they make a remote payment. However, PSD2 also covers the authentication of account holders when they access or use a payment account — for example, when they login to their bank account, change or add contact information or perhaps add an additional account holder. Any activity on a payment account that increases fraud risk requires strong customer authentication. Financial institutions have many different ways to check that someone using an account is the legitimate accountholder, but to meet the requirements of PSD2 their checks must cover two of three categories:
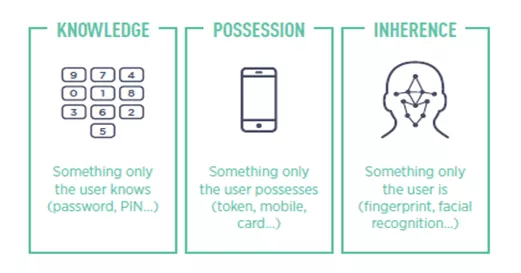
While account security is of paramount importance, the vast majority of people using accounts are the legitimate account holders. Increasing security to a level that they find using their accounts too difficult provides poor customer experience and can lead to customers changing their account providers. This means that financial institutions must balance the need for security with the need to provide legitimate customers with a good experience and they can do this through a process of adaptive authentication, which allows them to apply the right level of security to every interaction.
Customer communications for confirmation
Once a fraudster has accessed an account the game has not been lost. The more details they change on an account the more control they have, but before they make changes the bank has the contact information for the real accountholder. As well as authenticating customers wanting to make changes, banks can use real-time, automated, and two-way communications with their customers to confirm such actions are desired.
For example, if a change of address is requested then a text message can be sent to the mobile phone number on record asking the legitimate customer to confirm they want to make the change. If an attempt is made to change a mobile phone number a message through a banking app, email or even by letter, the institution can confirm that such changes are required by the legitimate accountholder.
Understanding criminal networks
Organized crime usually operates on a large scale; fraudsters are looking to take over as many accounts as they can. While this is a threat to a financial institution deemed to have poor defenses, it can also be an opportunity to identify accounts that have been taken over.
As with application fraud, criminals have limited contact information they can use to manage the accounts they are controlling. They recycle mobile numbers, emails, and addresses using the same contact information for multiple accounts under their control. By deploying link analysis across an account portfolio, banks can see where those connections are and use this as evidence to uncover criminal activity. Leveraging network analytics will even uncover connections that are several degrees removed.
Account Takeover Fraud – No Single Fix
The complexity of account takeover fraud means that financial institutions have to take a layered approach to prevention and detection. When and how fraud prevention solutions are deployed must be balanced with other factors such as customer experience and operational costs. Flexibility is key to both creating the necessary balance and evolving at least as fast as the fraudsters can.
How FICO Can Help You Fight Account Takeover Fraud
- Read about the 5 Keys to Using AI and Machine Learning in Fraud Detection
- Explore our solutions for application fraud
- Discover the power of FICO Falcon Fraud Manager
This is an update of a post from 2022.
Popular Posts

Average U.S. FICO Score at 717 as More Consumers Face Financial Headwinds
Outlier or Start of a New Credit Score Trend?
Read more
Average U.S. FICO® Score at 716, Indicating Improvement in Consumer Credit Behaviors Despite Pandemic
The FICO Score is a broad-based, independent standard measure of credit risk
Read more
Average U.S. FICO® Score stays at 717 even as consumers are faced with economic uncertainty
Inflation fatigue puts more borrowers under financial pressure
Read moreTake the next step
Connect with FICO for answers to all your product and solution questions. Interested in becoming a business partner? Contact us to learn more. We look forward to hearing from you.
