How to Build a Winning Enterprise Fraud Management Strategy
Enterprise fraud management can break down fraud prevention operational silos so that fraud and abuse can be tackled at the customer level, rather than just the account level

In the battle against financial fraud, technology and analytics are powerful weapons - but without a cohesive strategy to guide their deployment, even the most sophisticated tools fall short. An enterprise fraud strategy serves as the blueprint that transforms disparate fraud-fighting efforts into a coordinated, effective defence system that protects both the organization and its customers, whilst satisfying myriad of different fraud and scam regulatory requirements that constantly evolve and change the ways in which we approach fraud prevention.
What Is Enterprise Fraud Management?
‘Enterprise fraud management’ reflects a philosophy of centralized fraud management within a business. Enterprise fraud management should help break down fraud prevention operational silos so that fraud and abuse can be identified at the customer level, rather than just at an account or transactional level.
An enterprise approach to fraud management makes organizations more productive and versatile in preventing and detecting fraud across multiple product lines and channels, and enhances their ability to uncover fraud and account misuse that would have otherwise been missed.
The Evolution from Siloed to Enterprise Approach
Managing fraud across the enterprise is a constantly evolving challenge as new products, payment methods, and new fraud types and patterns emerge. This is especially true for the banking and financial services industries. There are many factors driving this evolution:
- The implementation of additional customer engagement channels introduces new opportunities for fraud exposure
- Less well-defended products/channels are vulnerable to attack by fraudsters, who target the weakest links in the chain
- Fraud schemes are increasing in sophistication, with global fraud rings and criminal syndicates implementing coordinated attacks
- Generative AI is fuelling an increase in new attack vectors at an unprecedented scale – from next gen bot attacks, through deepfakes, all the way to AI enhanced, self-evolving malware bots
- Organizational silos within banks can impede the ability to recognize enterprise-wide and/or cross-channel fraud assaults
- An increase in regulatory oversight from payment regulators and government agencies is dictating increased fiscal responsibility when protecting customer assets and identities
- Economic and cost of living pressures are driving customers to facility misuse and first-party fraud
- Many organizations are on digital transformation journeys, moving traditionally face-to-face and/or manual interactions and workflows to online and digital channels
Additionally, many banks are increasing their focus on customer experience. Creating and maintaining a positive customer experience throughout a fraud intervention is often of equal importance to the prevention and detection of fraud itself:
- Banks have realized that inadequacies in managing fraud and placing the onus on the customer to make contact and resolve fraud issues can undermine their ability to build valuable customer relationships and increase profitability
- Banks have also recognized that a balanced and coordinated set of fraud countermeasures are key to protecting customers, earning their trust, and secure long-term loyalty
- Today it is easier than ever for customers to change providers if they are unhappy with the service they receive, and it is also incredibly easy for customers to share both positive and negative experiences to a vast consumer audience via social media; as a result, banks must consider the impact that effective or poor fraud management practices may have on customer experience, and as a result, their reputation
Done well, enterprise fraud management balances fraud prevention with optimizing customer experience, in accordance with the bank’s risk appetite and operational capacity for working cases. This is achieved through consolidation of systems, teams / fraud functions and data, centralizing responsibility for managing fraud losses across multiple products, business units and engagement channels. As a result, banks have a 360° view of the customer and can execute tailored treatment strategies via customer-preferred communication channels.

Historically, organizations managed fraud within separate product lines—credit cards had their own fraud team and own fraud systems, online banking another, and mortgage fraud yet another. This fragmented approach created several critical vulnerabilities:
- Blind Spots: Fraudsters could exploit gaps between departments
- Inconsistent Customer Experience: Different fraud responses across products confused and frustrated customers
- Inefficient Resource Allocation: Duplicate efforts and technologies across departments
- Limited Intelligence Sharing: Valuable fraud patterns discovered in one area weren't communicated to others
The shift to enterprise fraud management addresses these challenges by creating what many leading banks call a centre of excellence - a unified fraud-fighting force that protects the entire organization and relies on sophisticated multi-use-case, multi-channel and multi-product fraud solution for profiling, decisioning and customer communication.
What Is an Enterprise Fraud Strategy?
An enterprise fraud strategy defines an organization's fundamental vision and approach to managing fraud risk consistently across multiple disciplines. It represents the strategic direction that guides every fraud management decision, from customer treatment to technology deployment. Unlike day-to-day tactical responses, fraud strategy establishes the overarching framework within which all fraud-fighting activities operate.
A well-crafted fraud strategy encompasses three critical focus areas:
- Intra-fraud lifecycle management focused on organizational and operational efficiency, such as:
- Unified leadership structure
- Resource optimisation
- Consistency in decisions and methodologies
- End-to-End process design
- Inter-departmental coordination by breaking down silos with other areas of the business, such as:
- Pre-campaign fraud risk assessment with Marketing
- Fraud-by-design review for a new product with Product Management
- Escalation procedures and warm transfer processes with Customer Services
- Sharing of data and strategies for first-party and bust-out fraud prevention with Credit Risk
- Joint mule profiling approaches for both scams and AML with Compliance teams
- Creation of Fusion Centers, where the connection between Enterprise Fraud and Cyber, Physical, Internal and AML threats is bridged over through systemic and aligned processes, data and tools
- External ecosystem management through vendor relationships, regulatory compliance and industry collaboration
The Cornerstone Elements of Fraud Strategy
While the vision for enterprise fraud management may be clear, translating that vision into actionable reality requires three foundational elements that serve as the bedrock of any successful fraud program. These cornerstones - fraud policy, risk appetite, and threat and vulnerability management - transform good intentions into measurable results. Without any one of these elements, even the most sophisticated analytics and operations will struggle to deliver consistent, strategic value.
1. Fraud Policy: Your North Star
The fraud policy document serves as the constitution for your fraud management program. It must clearly define:
- Ownership and Accountability: Who owns specific fraud-related activities across the organization
- Delegated Authority: Empowering rapid decision-making with clear authority levels
- Scope of Responsibility: Which activities are owned by the fraud team, which are shared, and which belong elsewhere
Critical topics and areas each fraud policy should be mutually agreed upon not just by the fraud team, but also the wider business areas. These include:
- Lead responsibility for internal and external fraud projects
- Budget ownership and forecasting authority
- Legal and regulatory compliance ownership
- New product development involvement
- Demarcation between fraud and credit losses
- Prosecution protocols and write-off procedures
Fraud policy should be reviewed and updated annually, with interim updates for significant organizational changes.
2. Risk Appetite: Setting the Boundaries
This is perhaps the most critical strategic decision is establishing the organization's fraud risk appetite. This framework balances fraud prevention with customer experience and operational efficiency. The risk appetite creates guardrails within which the fraud team should operate and be empowered to make decisions. It encompasses such core measures and KPIs as:
- Gross Fraud (basis points): The purest measure of fraud impact, representing total losses before recovery
- Net Fraud (basis points): Actual losses after all recovery efforts, feeding directly into P&L
- Intervention Rates: False positive ratios, decline rates and alert review rates for both account-level and transaction-level interventions
- Revenue Impact: Lost income from declined legitimate transactions
- Customer Experience: Net Promoter Scores and complaint volumes
One of the key objectives the fraud risk appetite should established is what is the “sweet spot” your organisation should be aiming for when it comes to fraud prevention – the balance between fraud loss prevention, customer impact and operational impact/constraints.
The actual KPI target, the guardrails within which the fraud area should operate will largely vary depending on the current fraud levels, effectiveness of the fraud solutions and its models, and the level of automation within fraud operations.
It’s down to you and your business partners within the organisation to collectively decide what the goal is – whether it’s preventing as much loss as possible, not interrupting too much of the business at the cost of higher losses, or perhaps finding the right balance based on very specific operational capacity within the fraud operations. FICO Fraud Domain Experts can help you understand what good and effective looks like in comparison to your peers across the globe.
3. Threat and Vulnerability Management
Modern fraud strategy requires continuous horizon scanning to identify and prepare for emerging threats. Organizations must maintain a dynamic threat assessment process that includes appropriate reporting, control functions, response procedures and effective day-to-day management approaches that cover:
Internal Risk Factors:
- New product launches and their fraud exposure
- Marketing campaigns that may attract fraudsters
- Resource constraints affecting fraud controls
- Technology infrastructure vulnerabilities
External Risk Factors:
- Regulatory changes and compliance requirements
- Economic conditions driving fraud behaviour
- Emerging fraud techniques and attack vectors
- Third-party vendor risks
It’s good practice to maintain a quarterly-updated threat horizon document with risk ratings and mitigation strategies for each identified threat.
Your Strategic Framework
With fraud policy, risk appetite, and threat management established as your strategic foundation, the next challenge is creating the organizational structures and processes that bring strategy to life. An effective strategic framework requires four interconnected components that transform high-level vision into operational reality.
1. Centre of Excellence
Almost every organisation is expected to tackle threats through what most regulators refer to as a "three lines of defence" approach, which includes:
- The first line of defence consists of the business units and operational management that own and manage risks as an integral part of their daily activities
- The second line of defence consists of risk management and compliance functions that provide oversight of the first line's risk-taking activities
- The third line is an independent internal audit function that provides an objective assessment of the effectiveness of the bank's risk management and governance processes
Whilst operating independent of each other structurally, each of those lines of defence can come together within their line of defence in a unified way, through what’s often referred to as a centre of excellence (CoE) that consolidates fragmented fraud prevention efforts into a unified force that delivers benefits across all products and channels, providing:
- Economies of Scale: Combined analytics and operations teams that flex based on fraud exposure
- Dynamic Response: Ability to quickly shift resources as fraud patterns change
- Holistic Visibility: Complete view of fraud across all products and channels
- Consistent Experience: Uniform customer treatment regardless of product or channel
Key steps for CoE Implementation:
- Appoint or elevate a senior Head of Enterprise Fraud reporting to C-suite – your voice at the table, driving a cohesive, unified message and vision for the entire fraud area
- Create distinct leadership roles for Strategy, Analytics, Operations, and MI
- Create an Enterprise Fraud Policy Document
- Develop standardized processes across all products
- Centralize fraud losses and monitoring into a dedicated ledger
2. Budget and Forecasting Excellence
Second, sophisticated budget and forecasting processes move beyond simple loss projections to create dynamic financial models that anticipate fraud trends and justify investments.
Key considerations:
- Use market and historical data intelligence to anticipate fraud trend changes
- Model and simulate various economic scenarios and their fraud impact
- Build in contingency for unexpected fraud attacks
- Link budget assumptions directly to risk appetite metrics
3. Program Management for Agility
Third, dedicated program management ensures coordinated execution across the dozens of initiatives required in modern fraud prevention, from new product launches to technology implementations.
A dedicated program management function ensures that these core responsibilities are taken care of:
- New Product Fraud Assessment: Coordinate cross-functional teams to evaluate fraud risks
- Technology Integration: Manage rollout of new fraud tools and systems
- Training and Awareness: Develop fraud education for staff and customers
- Quality Assurance: Implement consistent quality standards across all fraud operations
- Regulatory Compliance: Ensure all activities meet legal requirements
4. Customer-Centric Strategy Design
Finally, customer-centric design principles ensure that all fraud controls balance security with user experience, recognizing that the best fraud strategy is worthless if it drives customers away.
The Five Cs of Customer-Centric Fraud Management include:
- Cost: Understanding total fraud impact including customer lifetime value
- Clarity: Clear communication about fraud policies and customer obligations
- Consistency: Uniform treatment across all channels and products
- Communication: Optimized contact strategies that respect customer preferences
- Closure: Swift resolution with appropriate follow-up and protection
Customer Charter Example:
- Refund fraud losses within 24 hours for verified claims
- Answer 90% of fraud calls within 2 minutes
- Provide self-service resolution options for all channels
- Offer proactive fraud prevention tools at no cost
- Ensure 24/7 fraud support availability
Fraud Strategy Management Across the Customer Lifecycle
What should the fraud policy, risk appetite, the centre of excellence and all of the different fraud frameworks and processes actually encompass when it comes to different types of fraud?
There are typically six key stages of countermeasures deployed for enterprise fraud management across the customer lifecycle and managed by a unified team monitoring fraud at a customer level, across their entire relationship with the organisation, from start to finish.
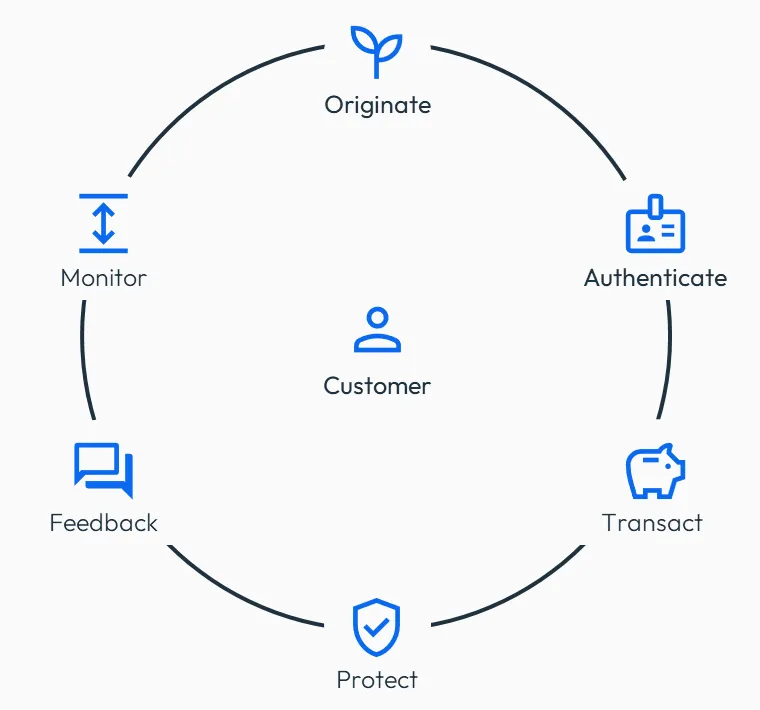
1. Originate - Fraud at the Point of Application (Application Fraud)
The customer lifecycle begins at the point of application for products and/or services.
- The application stage is commonly known as “pre-book” as the potential customer has not yet been approved and onboarded. The account is yet to be originated.
- Usually, banks deploy credit risk decisioning at this stage to assess the creditworthiness of a potential customer. This is the first control point and serves as the largest opportunity to prevent fraud from happening.
- Enterprise fraud management requires banks to have a consolidated application fraud defence framework, ensuring that all channels and products have both first-party and third-party fraud countermeasures. First-party fraud is where the customer themselves is intending to commit fraud against the bank, and third-party is where a fraudster may be using stolen identities or synthetic details, purporting to be a genuine applicant.
2. Authenticate - Fraud at Account Creation
Account creation is the second stage at which fraud countermeasures can be validated, and such validation usually occurs prior to the customer’s first statement / first month on book.
- Enterprise fraud management capabilities should focus on changes such as additional account holders, changes to demographic data, and addition of service capabilities or other products (e.g., activation of online banking, application for new personal loan product).
- Accounts which were considered borderline for eligibility, or marked as suspect but ultimately booked during stage 1, should be reviewed using post-book fraud monitoring capabilities.
3. Transact – Early-Life Fraud Monitoring
Early life fraud monitoring is the third stage of monitoring, with the focus typically placed on identifying and managing first-party fraud and account-level fraud risk.
- Fraud monitoring capabilities should be deployed at this stage to manage “hit and run” type fraud risk, where the fraudster typically disappears within the first three payments. Hallmarks of this modus operandi include high credit utilization / balance utilization in a short period of time.
- Banks should also review non-monetary activity on new accounts, to look for any changes in account or customer demographics post-onboarding.
4. Protect – Extended-Life Fraud Monitoring
Extended life fraud monitoring represents the monitoring of all risk types for tenured customers. Typically, this includes customers who have been tenured for three months or more.
- By this stage, a customer has started to accumulate substantial transaction and non-monetary activities which form the basis of a behavioral profile. This profile of genuine customer behavior is essential for ongoing fraud monitoring, as identification of activity and behavior misaligned with the customer profile is key to implementing effective protection against third-party fraud
- This is the stage where monitoring of real-time payment, credit and debit card transactions, and ability to make decisions in real-time on what sort of treatment or action is required is critical
- Ability to rely on consortium based machine learning models or development of your own artificial intelligence models that can be efficiently operationalized is key to the success of your fraud strategy
- Having access to specialized AI focused team that are either based within the fraud area, or are a shared resource within the financial organization, is becoming more and more popular
- From a first-party fraud perspective, the focus shifts to catching sleeper frauds; this is where a fraudster behaves like a legitimate user for an extended period of time before suddenly executing high-value fraudulent transactions and/or “busting out” (where they have no intention of repaying)
5. Feedback - Fraud Intelligence Feedback Loop
Fraudulent activity identified across any stage of the customer lifecycle should be leveraged to assist in the prevention of future fraud from occurring either pre-book or post-book. This means that banks should be capturing intelligence from multiple data points:
- Fraudulent transactions should be tagged as “fraud” for strategy development and analysis
- Lists should be maintained for known fraudulent entities. Such lists could include:
- Merchants
- Device IDs
- Phone Numbers
- Email Addresses
- Physical Addresses
- IP Addresses
- ….and more
- Cross-Industry intelligence from other banks and Payment Service Providers, telcos, fraud and crime prevention bodies, social media sites, and more, can be leveraged to increase fraud detection and prevention.
- External vendors may offer analytical services and/or models (e.g., transaction risk scoring, device risk scoring, biometric analysis, IP analysis, email address analysis etc.) which provide an extra layer of protection. These specialist services are continuously refined as service-users report confirmed fraud / confirmed genuine activity, allowing for better identification of anomalies outside of a regular customer’s profile (e.g., login via security code instead of face authentication), and/or outside of regular human behavior (e.g., automated attacks via bots may complete tasks on an application form in milliseconds, whereas humans may stay on a field for a few seconds and a page for a few minutes).
6. Monitor – Troubled-Life Fraud Monitoring
The final stage of fraud control, stage 6, is described as “troubled life”. This means that the account is in delinquency.
- Frauds not already identified during the customer lifecycle will naturally sit in collections queues and be ultimately written off
- Troubled life data is also a source of intelligence which can be used to create and refine first-party fraud definitions
- The aim of these definitions is to separate “normal” bad debt (e.g., customer getting into financial difficulty and unable to pay) from debt where the customer never had the intention to repay
- At this stage of the lifecycle it may not be possible to prevent losses from occurring, however it is sometimes possible to make partial or full recoveries
- It also allows the financial institution to be able to better classify bad debt vs fraud, allowing for appropriate focus and investment into the problem areas
Don’t Get Caught in the Rain with a Poor Approach to Enterprise Fraud Management
Moving forward, fraud strategy can no longer be reactive or tactical. The combination of sophisticated fraud attacks, regulatory pressure, and customer expectations demands a comprehensive strategic approach which relies on enterprise fraud management solutions.
Financial Institutions that develop and nurture robust enterprise fraud strategies — with clear policies, defined risk appetites, and customer-centric designs — position themselves not just to fight fraud more effectively, but to turn fraud management into a competitive advantage.
The most successful strategies recognize that fraud management isn't just about preventing losses, it's about building trust, enabling growth, and ensuring consistency.
As fraud continues to evolve, so too must our approaches, always keeping one step ahead while never losing sight of the customer experience that ultimately drives business success. And we need to be able to flex, be nimble and fast in our response at an enterprise level, not just in the siloed view of a single product or a channel.
How FICO Can Help You Build and Strengthen Your Enterprise Fraud Management
Popular Posts

Average U.S. FICO Score at 717 as More Consumers Face Financial Headwinds
Outlier or Start of a New Credit Score Trend?
Read more
Average U.S. FICO® Score at 716, Indicating Improvement in Consumer Credit Behaviors Despite Pandemic
The FICO Score is a broad-based, independent standard measure of credit risk
Read more
Average U.S. FICO® Score stays at 717 even as consumers are faced with economic uncertainty
Inflation fatigue puts more borrowers under financial pressure
Read moreTake the next step
Connect with FICO for answers to all your product and solution questions. Interested in becoming a business partner? Contact us to learn more. We look forward to hearing from you.
