How to Fight Scams Through Better Classification and Effective Tagging
Defining and understanding different scam typologies yields results when identifying and preventing authorized push payment fraud

As real-time payments have gained ubiquity authorized push payment fraud because of scams on both consumers and businesses have increased exponentially. Fraudsters are very aware of the differences between the tactics and messaging required to commit a scam compared to other types of fraud. They even vary their approach tailoring their techniques to the specific scam type.
The question arises: if fraudsters have classified how they target victims for different scams and use corresponding types of messaging, how effectively does your organization categorize scams, adjust your customer messaging, and identify and tag the different typologies in your data?
Not properly distinguishing scams from other types of fraud and not effectively defining and categorizing scams has several knock-on implications for the fraud department, the business as a whole and for customers:
- Incomplete understanding of the scale of the scams problem within your financial institution
- Firehose approach to scams education for customers
- Poor communication with customers due to inability to correctly identify potential scams
- Inability to effectively back test and carry out what-if scenarios on rules
- Less effective models and diminished fraud detection from consortium scam models
Defining and Documenting Scams Typologies
The starting point is ensuring that your fraud department has made and documented the distinction between transactional fraud typologies (account takeover, identity theft, Card Not Present (CNP), etc.) and scams or authorized push payment fraud. From there scams need to be categorized into different typologies (e.g. impersonation, investment, romance, etc.). Each type should be clearly documented and understood.
For those organizations that have not yet established their typologies there are multiple resources that can help. These include:
- UK Finance – Half Year Fraud Update 2023 – Eight Scam Types
- European Banking Association – EBA Fraud Taxonomy V4.0
- Australian National Anti-Scam Centre – Types of Scams
New scam techniques are introduced on a fairly regular basis. One need only consider the rise of cryptocurrency scams in the past few years. While this type of scam has seen explosive growth, in reality it is essentially just another form of an investment scam. When defining your list of categorizations, you should be mindful of over-classification of scam types. If further classification is required for customer communication, reporting or further analytics, alternative data elements (e.g. Merchant or Beneficiary Types) can be utilized.
Once you have defined and documented your scams typologies you will need to put them into practice by enabling analysts to tag any alerts based on your scam typologies. Furthermore, you’ll need to ensure that your investigative/claims process and their corresponding data warehouses can accommodate scams information (distinction between fraud & scam, scam typology, etc.).
With these elements enabled, you will be able to put into place a Data Intelligence Loop for scams.
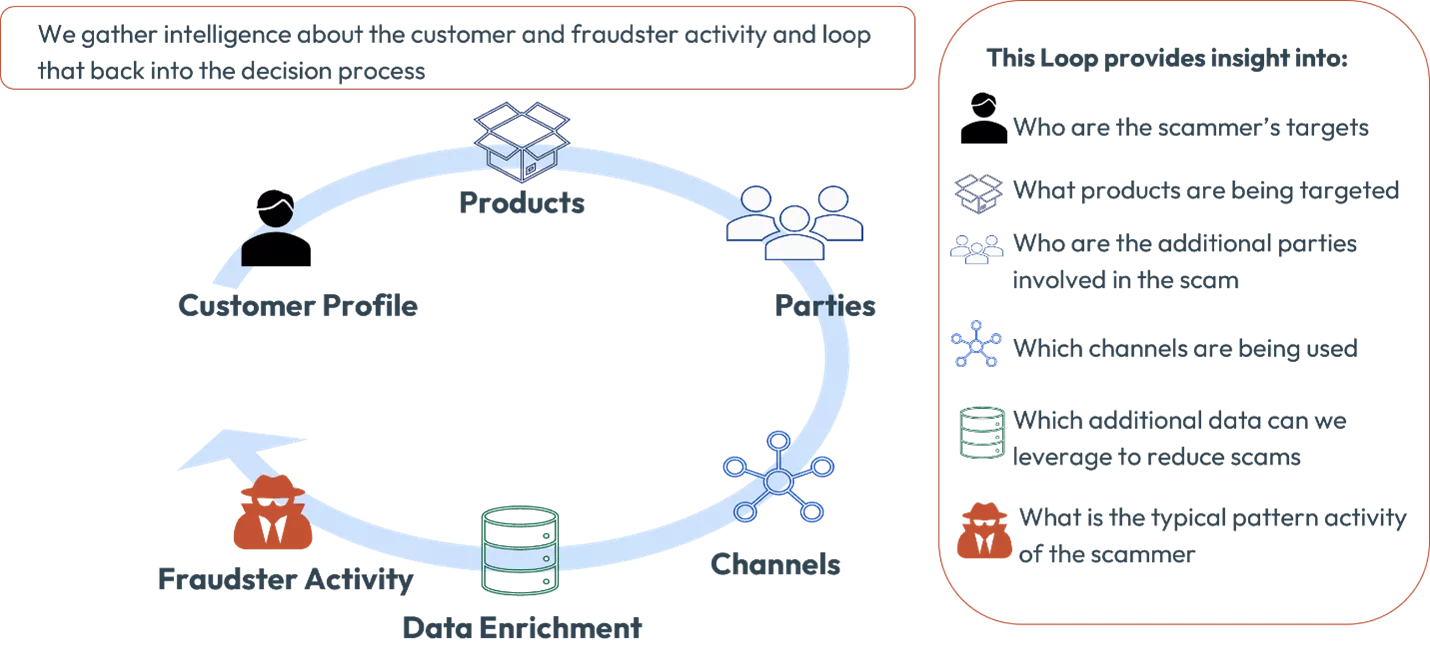
This Data Intelligence Loop facilitates continuous improvement of Fraud Controls and therefore drives down fraud losses and minimizes customer friction by giving you the information you need to make better decisions. Without this in place you are flying blind when it comes to building out and refining strategies to combat scams.
Once your fraud organization has defined, documented, and put into practice this Data Intelligence Loop there are a number of benefits including:
Better Insights
With effective data tagging for scams and supporting data storage capabilities in place, your organization can utilize this data to gain better insights about scams. In turn this leads to the added benefits of:
- Better reporting – Without the ability to tag alert dispositions according to your scam typologies, understanding the scope and nature of the scams problem will remain guesswork at best. Tagging data unlocks your ability to create reports on scam activity. This is not only important from an internal need, but as we’ve highlighted in a number of recent blog posts by myself about trends in Latin America and my colleague Szymon Morytko on APJ, we’ve seen a number of jurisdictions recently pushing financial institutions to share data on scams.
- Compelling business case – Better reporting forms the basis for building a better business case for tackling scams. Whether it is the use of a scams model, better client communication tools or procurement of third-party data to enhance your decisions, they all require a business justification for the investment. If you can’t quantify the problem and the impact on your financial institution and your customers, then no amount of discussion will justify the extra budget.
- Clear understanding of actual client education needs – Taking a scattershot approach to the education of clients on scams is a waste of resources and money. If we are better able to understand the types of scams clients are being targeted by, then we can focus our resources on those needs, rather than a generalist approach to Scams Education.
Better Decisions
Better decisions are driven by better insights. By gathering additional information about scams we can fine-tune or even develop new strategies to tackle scams, including:
- Focused rules – The tactics used in a scam by a fraudster are different than other transactional fraud topologies. We cannot expect that the rules for Card Not Present (CNP) fraud or Account Takeover to be as effective in covering scams as targeted rules specific to scams. With tagging in place and the ability to backtest specifically for scams, we can fine-tune or devise new rules to target scams and yield better results for scam prevention.
- Ability to leverage models – By tagging scams within your data you can build your own custom models or utilize vendor-supplied models. Additionally, the tagging of scams allows you to contribute to and better utilize scams consortium models. This means you will benefit from the experience of other financial institutions in identifying existing scams and scams that may not have yet reached your financial institution.
- Targeted queues – The deployment of scams specific rules and models enhances the treatment of alerts as they now can be routed to scam specific queues, rather than more generalized queues. The alert can then be dispositioned by an analyst who is knowledgeable in the investigation and treatment of potential scams and their victims.
Better Communications with Clients
Effective customer communication is all about getting the right message to the customer at the right time. Below we have an example of the traditional messaging we see when a transaction is deemed to be suspicious. This type of message can be effective in preventing traditional fraudulent transactions, such as CNP fraud or card skimming.

However, we should question how effective this type of message is when it is not the fraudster carrying out the transaction, but rather the customer. The customer may believe that the transaction they are carrying out is legitimate or may even have received coaching from the scammer on what to do when they receive this type of message.
When we suspect a customer is being scammed, we should use targeted messaging that breaks the fraudsters spell and drives consumers to think about whether the transaction is in fact legitimate.
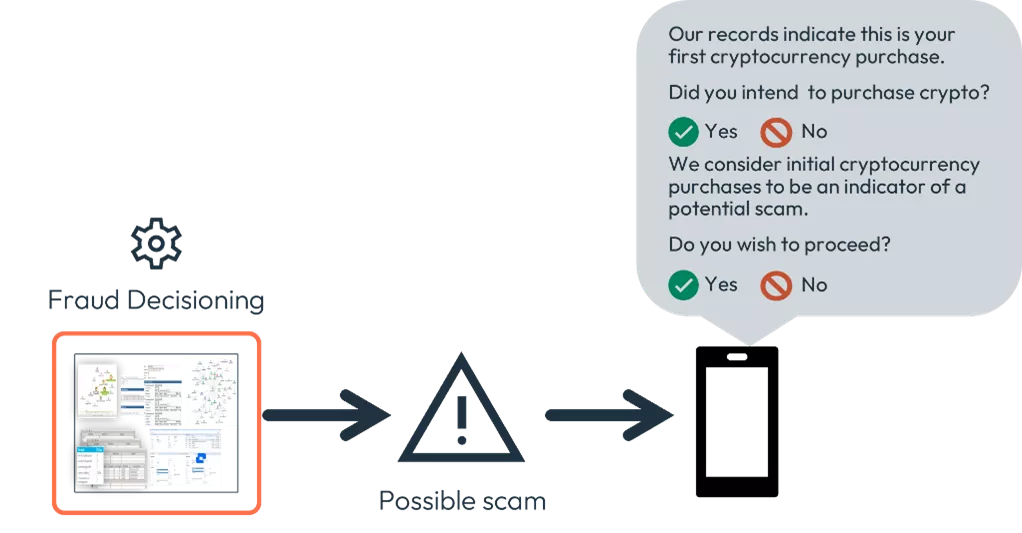
As we see in the example message above, we are attempting to get the customer to understand the potential risks of the transaction and take a moment to consider their actions. This is tailored, customer-specific, transaction specific type of intervention, which is exactly what is what the UK’s Payment Service Regulator (PSR) called for in their Consumer Standard of Caution Exception Guidance document.
It is not just the messaging at the time of a potential scam transaction that is important. Client communications around scams will become even more crucial as more formalized liability models come into place due to regulation like the UK’s 50/50 liability proposal. As part of the claims management process, receiving financial institutions will need to respond to the sending financial institutions’ information requests.
This potentially requires additional information or attestation be requested from the client. This must be considered with the expectation of rapid response times enforced by regulation. It is paramount that financial institutions start to consider how they will be able to manage this type of additional, rapid communications requirement as soon as possible.
FICO’s fraud consulting team stands ready to help customers globally combat scams through the use of fraud decisioning rules, scams models and automated, bespoke communications methods.
How FICO Helps Detect and Prevent Scams
- Learn how FICO helps financial institutions prevent scams
- Explore how Dock has used real-time customer communications to stop more fraud.
- Read about FICO’s award winning, machine learning-powered retail banking model with scam detection score
- Download the FICO 2023 Scams Impact Survey
Popular Posts

Average U.S. FICO Score at 717 as More Consumers Face Financial Headwinds
Outlier or Start of a New Credit Score Trend?
Read more
Average U.S. FICO® Score at 716, Indicating Improvement in Consumer Credit Behaviors Despite Pandemic
The FICO Score is a broad-based, independent standard measure of credit risk
Read more
Average U.S. FICO® Score stays at 717 even as consumers are faced with economic uncertainty
Inflation fatigue puts more borrowers under financial pressure
Read moreTake the next step
Connect with FICO for answers to all your product and solution questions. Interested in becoming a business partner? Contact us to learn more. We look forward to hearing from you.
