Understanding Fraud Detection to Safeguard Financial Services in an Ever-Changing Threat Landscape
This comprehensive guide explores the multifaceted domain of fraud detection, including specific techniques and their practical implementation

The scope and scale of modern fraud is staggering. Criminals are inflicting huge financial losses on both customers and institutions, while siloed processes and lack of advanced detection can erode customer trust and compromise institutional reputations. In the regulated world of financial services, the integrity of every transaction and the security of every customer account are paramount. For fraud management practitioners and buyers, a deep, nuanced understanding of fraud detection - from foundational principles to cutting-edge applications - is critical.
This comprehensive guide explores the multifaceted domain of fraud detection, including specific techniques and their practical implementation. We will also explore how FICO uses advanced analytics, machine learning, and a holistic, end-to-end approach to fraud management to combat emerging threats and neutralize them before significant damage occurs.
What is Fraud Detection? Core Concepts and Principles
At its core, fraud detection is the process of identifying and preventing deceptive practices designed to obtain financial or other gains through illicit means. It encompasses a wide range of activities, from monitoring individual transactions to analyzing broad behavioral patterns, to uncovering suspicious activities or malicious actors before they cause significant harm. For financial institutions, fraud management means safeguarding customer accounts, preventing unauthorized transactions, identifying and intervening in transactions that may be associated with criminal activity, and protecting the institution’s assets and reputation.
Consider credit card fraud. A customer makes a purchase online. A strong fraud detection system immediately analyzes this transaction against a wealth of historical data, including the customer's typical spending habits, geographical location, transaction size, merchant type, and device used. If the system detects out-of-pattern spending, the transaction originates from an unusual location, or use of a device not previously associated with the account, it flags the transaction as potentially fraudulent. This flag triggers further investigation or an immediate hold on the transaction, protecting the customer and the institution.
The primary objectives of a fraud detection framework are to accurately identify genuine fraud and to minimize false positives, when legitimate transactions are incorrectly flagged as fraudulent. A fraud detection system that errs too often on the side of caution can frustrate customers and lead to lost business, while a system that misses too much fraud exposes the institution to unacceptable risks and losses.
What Is The Typical Fraud Detection Process?
- Data Collection: Gathering vast amounts of data from various sources, including transaction histories, customer profiles, behavioral data, device information, and third-party risk intelligence.
- Anomaly Detection Modeling: Applying analytical techniques, such as machine learning algorithms, to identify patterns indicative of fraud by pinpointing deviations from established norms or expected behavior. These anomalies are the initial signals of potential suspicious activities.
- Analysis and Decisioning: Developing risk-based strategies leveraging the anomaly detection modeling and other data to determine whether to approve, deny, or further review a transaction.
- Alert Generation: When the analysis and decisioning reaches a certain risk threshold, the system generates an alert, notifying human analysts or triggering automated actions such as contacting the customer or blocking a transaction.
- Investigation: Fraud analysts review the priority alerts, gather additional context, and contact the customer to determine whether the activity is indeed fraudulent. Based on their findings, a decision is made to block or unblock the account, reissue a card, or other actions.
- Feedback Loop: The outcomes of investigations are fed back into the system to refine rules and retrain machine learning models, ensuring continuous improvement and adaptation to new fraud patterns.
The Key Principles of Fraud Detection
- Accuracy: The ability to correctly identify transactions as fraudulent or legitimate, minimizing both false positives and false negatives.
- Speed (Real-Time): The ability to process and analyze massive volumes of transactions in milliseconds is vital to preventing fraud during the authorization process.
- Adaptability: The capacity of the system to evolve and learn from new data, direct feedback, and detect emerging fraud schemes.
- Explainability: Understanding why a particular transaction was flagged as suspicious is crucial for regulatory compliance and effective investigation.
- Scalability: The system must be able to handle ever-increasing volumes of data and transactional volume without degradation in performance.
Why Fraud Detection Is Imperative for Financial Services
The financial services industry is a prime target for malicious actors. Because banks and other financial service providers deal with vast sums of money and sensitive customer data, they face an unrelenting barrage of criminals attempting to exploit vulnerabilities. The need for holistic enterprise fraud management systems has never been greater, and continues to be driven by escalating fraud volumes, increasing fraudster sophistication, and changing regulatory requirements.
Fraud losses are substantial and multifaceted. Beyond the direct theft of funds, institutions incur significant costs associated with investigations, chargebacks, operational overhead, and potential regulatory fines, which can impact the bottom line and strain resources. In addition, a single high-profile fraud incident can severely tarnish an institution's reputation, leading to a loss of customer trust and market share. Customers expect their financial providers to safeguard their assets and data; any breach of this trust can result in a mass exodus and a prolonged struggle to rebuild credibility.
Regulatory bodies worldwide impose strict requirements on financial institutions to implement effective controls to mitigate financial crime risks. Failure to comply can result in hefty fines, legal penalties, and severe operational restrictions, which means an institution's investment in enterprise fraud detection and management is both a good business decision and a regulatory obligation.
Fundamentally, fraud detection is the strategic defense mechanism that protects an institution's financial health, safeguards its customers, and upholds its standing in the market. Fraud detection is not reactive, but a proactive, real-time shield, constantly working to identify and intervene against criminal activities before they develop into significant losses.
Fraud is Constantly Evolving – Detection Systems Must Keep Up
Fraud is in a state of perpetual evolution. Fraudsters are agile, constantly adapting their methods to circumvent existing security measures and exploit new technologies like generative AI. What was effective fraud management yesterday may be obsolete tomorrow, which means organizations need dynamic fraud detection capabilities that can learn, adapt, predict, and identify new fraud patterns. Let's examine some of the different types of established and emerging frauds.
Payment Fraud
Payment fraud represents a significant portion of all fraudulent transactions and typically involves unauthorized access or manipulation of payment instruments.
- Card-Not-Present (CNP) Fraud: This occurs when fraudsters use stolen card information (obtained via data breaches, phishing, malware, and other means) to make purchases without having the physical card.
- Account Takeover (ATO): With account takeover fraud, a fraudster gains unauthorized access to an existing account, often through phishing, credential stuffing, or malware. Once in control, they can take actions like changing contact information or making unauthorized purchases. Behavioral analytics play a crucial role, particularly non-monetary transaction analysis such as detecting logins from new devices or locations or changes in personal details.
- Authorized Push Payment Fraud (APP): Authorized push payment fraud, commonly known as scams, happens when victims are tricked into authorizing payments or initiating wire transfers to fraudsters. This tactic has continued to grow globally : the FBI’s annual IC3 report tallied an average of 836,000 fraud complaints per year since 2020, or more than 4 million total, totaling $50.5 billion in losses. The latest report from the Global Anti-Scam Alliance estimates 2024 losses globally at $1 trillion.
- Digital Wallet Fraud: Digital wallet fraud occurs when digital wallets are compromised through phishing, malware or social engineering, to allow fraudsters to load stolen credentials for spending.
- Account Compromise: Fraudsters use deceptive communications (email, SMS, voice calls) to phish/smish/vish customers accordingly into revealing login credentials or other sensitive information. Once credentials are stolen, they gain unauthorized access to online accounts or make fraudulent purchases.
- Malware-Driven Fraud (Trojans, Ransomware): Malicious software installed on a user's device can intercept banking credentials, manipulate transactions, or even take control of the device to perform unauthorized actions.
Application Fraud
Application fraud occurs when individuals provide false information to obtain financial products, often leading to financial losses for institutions.
- Synthetic Identity Fraud: This sophisticated scheme involves creating a new identity using a mix of real and fabricated personal information (e.g., a real Social Security number combined with a fake name and date of birth). These synthetic identities are then used to open accounts, build credit history, and eventually "bust out" by maxing out lines of credit and disappearing. Synthetic identities are challenging to detect because the identity has sufficient legitimate information to pass traditional checks. Detection often requires advanced network analytics to identify connections between synthetic identities and shared fraudulent attributes, as well as behavioral analysis that flags fraud signals like rapid credit seeking.
- First-Party Fraud (Bust-Out Schemes): This is where legitimate customers intentionally defraud financial institutions. They open accounts, use them normally to build trust, and then maximize the credit lines with no intention of repayment, effectively "busting out" with the borrowed funds. Detecting first-party fraud involves analyzing the complete lifecycle of an account, looking for patterns of rapid credit utilization after a period of normal behavior, changes in financial habits, or attempts to obtain multiple credit products simultaneously before the bust-out.
- Third-Party Fraud: Third-party fraud occurs when an unknown or unauthorized entity commits identity fraud against individuals. Fraudsters use personally identifiable information obtained through data breaches or social engineering to bypass fraud defenses and open fraudulent accounts or secure credit in another individual’s name.
FICO's Ongoing Commitment to Fraud Detection
FICO has more than 30 years of fraud-fighting experience and is deeply committed to fraud detection. FICO offers advanced AI/ML-driven enterprise fraud management solutions that protect billions of accounts and transactions globally. Some 4 billion of the world’s payment card accounts are protected by FICO, which has developed 100+ fraud detection patents.
Behavioral Analytics
Behavioral analytics use machine learning to understand and anticipate behaviors across each aspect of a transaction. The information is tracked in profiles that represent the behaviors of each individual, merchant, account, or device. These behavioral profiles are updated with each transaction in real time to create analytic characteristics that predict future behavior. FICO’s robust enterprise fraud management capabilities combine analytic models and behavioral profiles to deliver insights about evolving transaction patterns in real time.
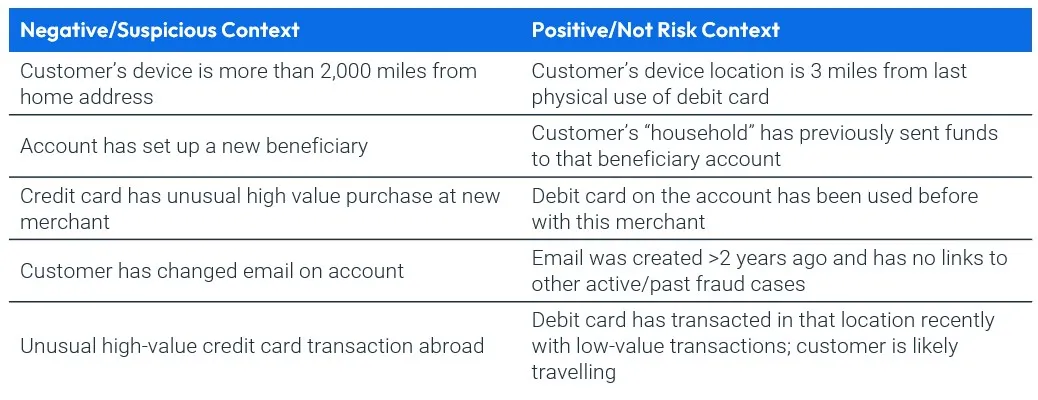
Authorized Push Payment Fraud
FICO helps financial institutions detect and prevent APP fraud thanks to an award-winning scam detection score. The model uses AI and machine learning to evaluate customer-specific archetypes based on their payment history to determine if the payment has a high propensity to be a normal transaction or an abnormal, potential scam payment. Additional insights from the award-winning FICO® Scam Signal can help institutions use real-time telephony signals to further refine decisions about specific transactions and whether they are potentially associated with a scam payment.
Enterprise Fraud Management
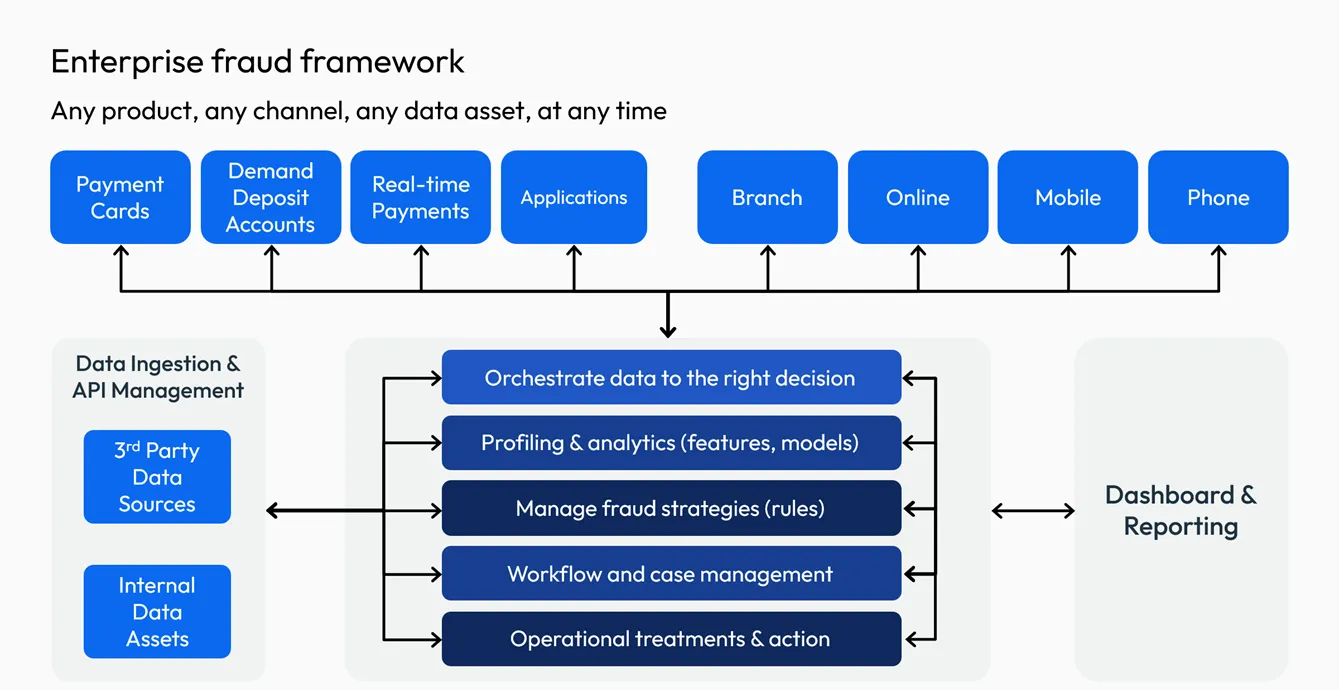
Enterprise fraud management reflects FICO's philosophy of centralized fraud management. Enterprise fraud management helps break down silos so that fraud can be identified wherever it happens in the customer lifecycle. FICO's approach is transforming fraud-fighting efforts by eliminating siloed, disconnected systems and giving institutions a centralized, coordinated, holistic system that protects both the organization and its customers, as recognized by the Chartis analyst report.
FICO’s Positioning – Enterprise Fraud Solutions, 2025, Chartis Research
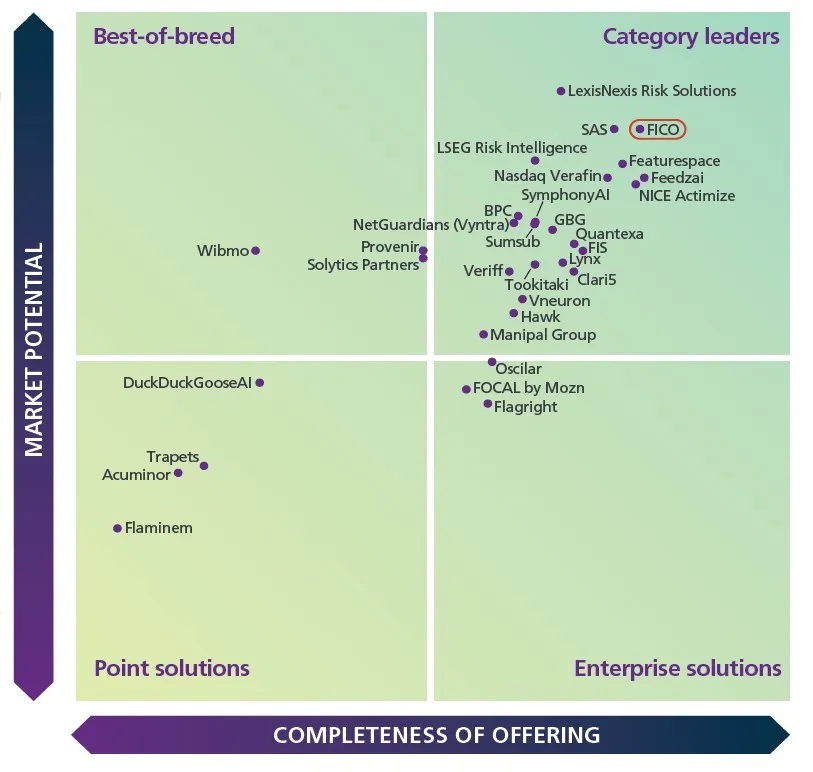
A Continuous Pursuit of Financial Security
Fraud detection in financial services requires adaptive, multi-layered defenses against sophisticated threats. Effective fraud prevention relies on people, processes, policy, and technology. Advanced AI and machine learning enable real-time transaction monitoring and accurate risk scoring, but implementing these systems involves choosing the right technology, building skilled teams, and meeting regulatory and privacy requirements. The time invested in choosing and deploying the right fraud detection solution is worth it, as it will result in reduced losses, greater trust, and improved efficiency.
How FICO Can Help You Build and Strengthen Your Enterprise Fraud Management
- Read Beyond Point Solutions: Orchestrating the Future of Fraud Prevention
- Download Chartis Vendor Spotlight: Enterprise and Payment Fraud Solutions, 2025
- Read The 6 "E"s of Enterprise Fraud Management
- Download the Scam Signal solution sheet to read more about how FICO can mitigate APP scams with real-time detection and intervention
- Explore FICO’s fraud solutions
Popular Posts

Business and IT Alignment is Critical to Your AI Success
These are the five pillars that can unite business and IT goals and convert artificial intelligence into measurable value — fast
Read more
Average U.S. FICO Score at 717 as More Consumers Face Financial Headwinds
Outlier or Start of a New Credit Score Trend?
Read more
Average U.S. FICO® Score at 716, Indicating Improvement in Consumer Credit Behaviors Despite Pandemic
The FICO Score is a broad-based, independent standard measure of credit risk
Read moreTake the next step
Connect with FICO for answers to all your product and solution questions. Interested in becoming a business partner? Contact us to learn more. We look forward to hearing from you.
